When it comes to monitoring IoT devices behind firewalls in AWS, you're stepping into a realm where innovation meets security. Picture this: your IoT devices are silently working behind the scenes, collecting data, processing insights, and sending updates. But what happens when they're tucked away behind a firewall? How do you ensure they're running smoothly without compromising your network's safety? That's the challenge we're diving into today, and trust me, it's a fascinating journey.
In the world of cloud computing, AWS has become the go-to platform for businesses of all sizes. Its scalability, flexibility, and security features make it a top choice for deploying IoT solutions. But here's the kicker—when you throw firewalls into the mix, things get a little more complicated. That's why understanding how to monitor IoT devices behind firewalls in AWS is not just a nice-to-have skill; it's a must-have.
So, whether you're a tech-savvy professional or just dipping your toes into the IoT waters, this article has got you covered. We'll explore everything from the basics to the advanced strategies that will help you keep your IoT devices humming along, even when they're tucked safely behind those firewalls.
Read also:Wwwmasahubcom Your Ultimate Destination For Tech Insights And Digital Solutions
Before we dive into the nitty-gritty, let's break down the key sections of this article for you. It's like a treasure map to help you navigate through the content effortlessly. Here's what you can expect:
- Biography of Key Concepts
- IoT Device Monitoring Overview
- Understanding Firewalls in AWS
- Effective Monitoring Methods
- Top Tools for Monitoring
- Security Best Practices
- Data Collection and Analysis
- Troubleshooting Tips
- Scaling Your Monitoring
- Final Thoughts
Biography of Key Concepts
Before we jump into the technical details, let's take a moment to understand the key players in this story. IoT devices, firewalls, and AWS are like the dynamic trio that keeps your digital world running smoothly.
IoT devices are the workhorses of the modern tech landscape. They collect data, send updates, and sometimes even control other devices. Firewalls, on the other hand, act as the bouncers at a club, deciding who gets in and who doesn't. And AWS? Well, it's the stage where all the action happens, providing the infrastructure and tools needed to make everything work.
Here's a quick rundown of the key players:
| Concept | Description |
|---|---|
| IoT Devices | Devices that connect to the internet to send and receive data. |
| Firewalls | Network security systems that monitor and control incoming and outgoing network traffic. |
| AWS | A cloud computing platform offering a wide range of services. |
IoT Device Monitoring Overview
Why Monitoring Matters
Monitoring IoT devices is not just about keeping an eye on them; it's about ensuring they're performing as expected. Think of it like checking the oil in your car. You don't want to wait until something goes wrong before you take action, right?
When it comes to IoT devices behind firewalls in AWS, monitoring becomes even more critical. You need to ensure that the firewall isn't blocking essential communications, while also keeping an eye out for any suspicious activity.
Read also:Haley Hazey Onlyfans The Ultimate Guide To Her Journey Content And Success
Understanding Firewalls in AWS
Types of Firewalls
AWS offers several types of firewalls, each with its own strengths and weaknesses. The most common ones are:
- Network Firewalls: These control traffic at the network level, ensuring that only authorized traffic gets through.
- Application Firewalls: These focus on the application layer, protecting your IoT devices from application-specific threats.
Choosing the right firewall for your IoT devices depends on your specific needs and the level of security you require.
Effective Monitoring Methods
Active vs. Passive Monitoring
There are two main approaches to monitoring IoT devices: active and passive. Active monitoring involves sending regular checks to your devices to ensure they're functioning correctly. Passive monitoring, on the other hand, involves observing the traffic without interfering with it.
Both methods have their pros and cons, and the best approach often involves a combination of both.
Top Tools for Monitoring
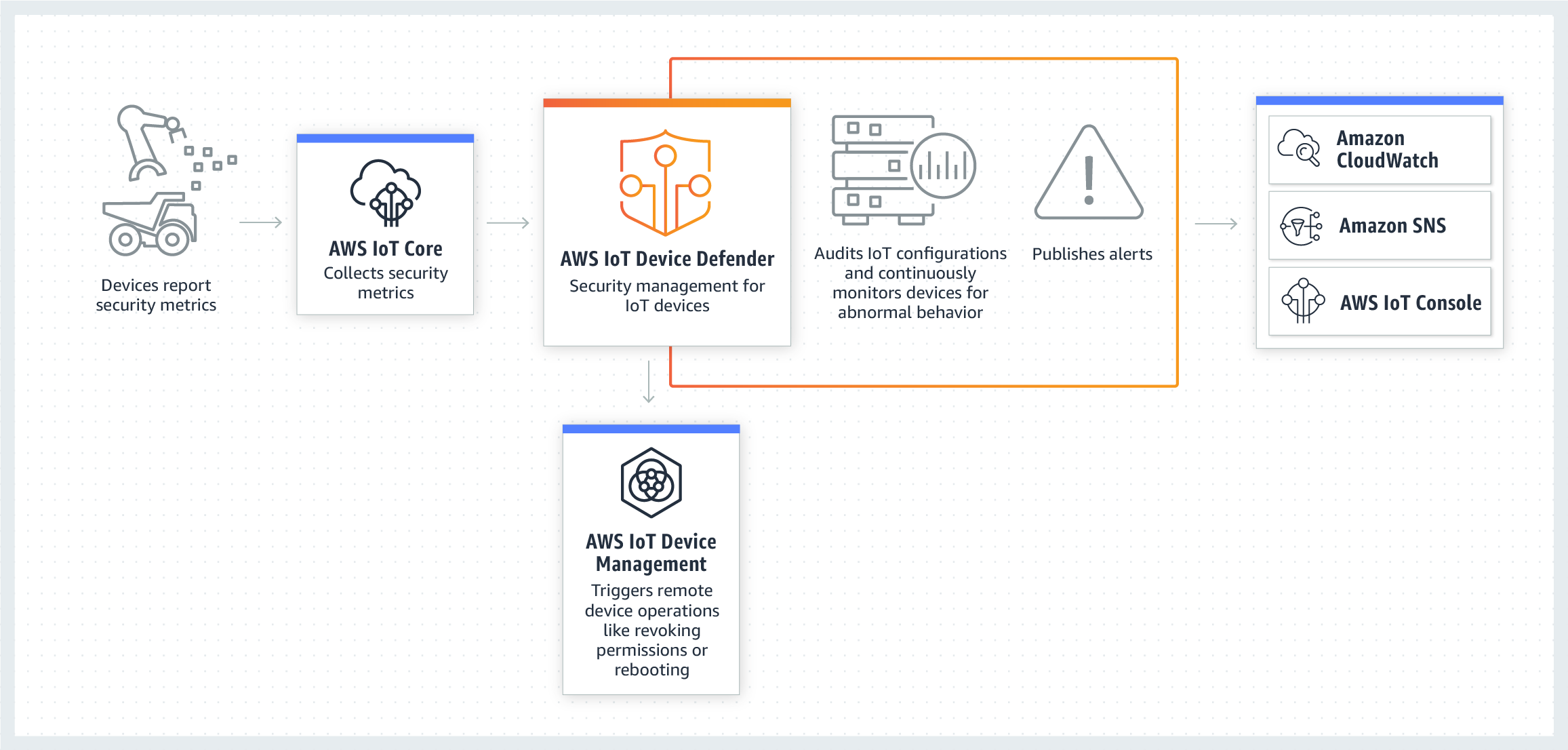
AWS IoT Core
AWS IoT Core is a managed cloud service that lets connected devices easily and securely interact with cloud applications and other devices. It's like having a personal assistant for your IoT devices, keeping track of everything they're doing.
Some of the key features of AWS IoT Core include:
- Device management
- Message brokering
- Security features
Security Best Practices
Encryption and Authentication
When it comes to IoT devices behind firewalls in AWS, security should always be at the forefront of your mind. Encryption and authentication are two of the most effective ways to protect your devices from unauthorized access.
Encryption ensures that even if someone intercepts your data, they won't be able to read it without the proper key. Authentication, on the other hand, verifies that the devices communicating with each other are who they say they are.
Data Collection and Analysis
Using AWS Lambda for Data Processing
Data collection is a crucial part of monitoring IoT devices. AWS Lambda can help you process this data in real-time, allowing you to make informed decisions quickly.
Here's how AWS Lambda can help:
- Automate data processing tasks
- Scale automatically to handle large amounts of data
- Integrate seamlessly with other AWS services
Troubleshooting Tips
Common Issues and Solutions
Even the best-laid plans can go awry, and troubleshooting is an essential part of maintaining your IoT devices. Here are some common issues and how to solve them:
- Connection Problems: Check your firewall rules and ensure that the necessary ports are open.
- Data Loss: Verify that your data collection mechanisms are working correctly.
- Performance Issues: Optimize your device settings and consider upgrading your hardware if necessary.
Scaling Your Monitoring
Planning for Growth
As your IoT deployment grows, so too will your monitoring needs. Planning for scalability from the outset will save you a lot of headaches down the line.
Here are some tips for scaling your monitoring:
- Use scalable AWS services like DynamoDB for data storage.
- Implement automated scaling policies to handle increased loads.
- Regularly review and update your monitoring strategies to ensure they remain effective.
Final Thoughts
Monitoring IoT devices behind firewalls in AWS might sound like a daunting task, but with the right tools and strategies, it's entirely manageable. From understanding the basics of firewalls to implementing advanced monitoring techniques, this article has covered it all.
So, what's next? Take what you've learned here and apply it to your own IoT deployment. And don't forget to share your experiences and insights with the community. The more we learn from each other, the stronger our IoT ecosystems become.
And hey, if you found this article helpful, drop a comment or share it with your network. Let's keep the conversation going and continue to innovate in the world of IoT and AWS.